- Configuration management databases (CMDB) are a lot of work to build and maintain. Starting down this process without the right tools, processes, and buy-in is a lot of work with very little reward.
- If you decide to just build it and expect they will come, you may find it difficult to articulate the value, and you will be disappointed by the lack of visitors.
- Relying on manual entry or automated data collection without governance may result in data you can’t trust, and if no one trusts the data, they won’t use it.
Our Advice
Critical Insight
- The right mindset is just as important as the right tools. By involving everyone early, you can ensure the right data is captured and validated and you can make maintenance part of the culture. This is critical to reaching early and continual value with a CMDB.
Impact and Result
- Define your use cases: Identify the use cases and prioritize those objectives into phases. Define what information will be needed to meet the use cases and how that information will be populated.
- Understand and design the CMDB data model: Define services and undiscoverable configuration items (CI) and map them to the discoverable CIs.
- Operationalize configuration record updates: Define data stewards and governance processes and integrate your configuration management practice with existing practices and lifecycles.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
9.0/10
Overall Impact
$48,737
Average $ Saved
21
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Aipso
Guided Implementation
10/10
$34,250
5
Municipality of Chatham-Kent
Workshop
8/10
$10,000
20
Scott was an excellent facilitator and helped the team visualize the benefits of a CMDB and navigate the difficult work of framing the project and ... Read More
Virginia Information Technologies Agency
Workshop
9/10
$137K
50
Best: Having dedicated time (M-F) to talk through issues with knowledgeable Info-Tech staff to keep the team focused. Info-Tech team had a well-str... Read More
Mexichem Servicios Administrativos S.A. de C.V.
Workshop
9/10
$13,700
10
The best is the predefined method, and the worst, it could be more adapted to the real Orbia environment, but it was done enough, so it was not tha... Read More
Lease Crutcher Lewis
Guided Implementation
8/10
N/A
N/A
Your Analyst was very helpful and also able to pivot through a difficult topic as we asked questions. Very knowledgeable. We are just exploring how... Read More
Point32Health
Guided Implementation
8/10
$34,099
20
Point32Health
Guided Implementation
8/10
$30,999
55
American Honda Motor
Guided Implementation
9/10
N/A
N/A
Best parts: Ken's knowledge and preparedness for every meeting. Helpful recommendations. Getting an unbiased opinion. Information Ken provided help... Read More
University of Exeter
Workshop
8/10
$174K
10
The workshop was well run, with good facilitation, and gained participation from even the most difficult parts of the audience. The best part of t... Read More
Griffith University
Guided Implementation
10/10
$29,391
20
No worst part - all info was very valuable and was presented in a manner that was easy to understand - thank you!
Akin Gump Strauss Hauer & Feld LLP
Guided Implementation
8/10
N/A
N/A

Configuration Management
A CMDB is only as valuable as the process it supports.
This course makes up part of the Infrastructure & Operations Certificate.
- Course Modules: 7
- Estimated Completion Time: 80 minutes
Workshop: Harness Configuration Management Superpowers
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
Module 1: Service configuration management (SCM) strategy
The Purpose
- Define the scope of your service configuration management project.
- Design the program to meet specific stakeholders needs
- Identify project and operational roles and responsibilities.
Key Benefits Achieved
- Designed a sustainable approach to building a CMDB.
Activities
Outputs
Introduction.
Define challenges and goals.
Define and prioritize use cases.
Identify data needed to meet these goals.
Define roles and responsibilities.
- Roles and responsibility matrix
- Data & reporting use cases based on stakeholder requirements
Module 2: CMDB data structure
The Purpose
- Build a data model around the desired use cases.
- Identify the data sources for populating the CMDB.
Key Benefits Achieved
- Identified which CIs and relationships will be captured in the CMDB.
Activities
Outputs
Define and prioritize your services.
Evaluate CMDB default classifications.
Test configuration items against existing categories.
- List of CI types and relationships to be added to default settings
Build a data model diagram.
- CMDB data model diagram
Module 3: Process design
The Purpose
Key Benefits Achieved
- Built a right-sized approach to configuration record updates and data validation.
Activities
Outputs
Define processes for onboarding, offboarding, and maintaining data in the CMDB.
Define practices for configuration baselines.
Build a data validation and auditing plan.
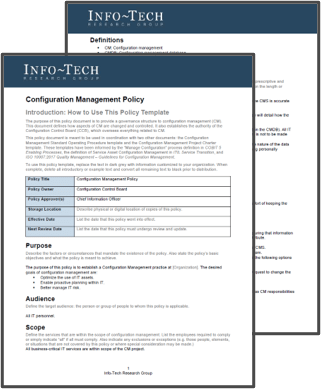
Build configuration management policies.
- Documented processes and workflows
- Data validation and auditing plan
- Policy for configuration management
Module 4: Communications & roadmap
The Purpose
Key Benefits Achieved
- Metrics program defined
- Communications designed
Activities
Outputs
Define key metrics for configuration management.
Define metrics for supporting services.
Create a communications plan.
Build a roadmap
- Roadmap for next steps
- Communications documents













 Implement Hardware Asset Management
Implement Hardware Asset Management
 Implement Software Asset Management
Implement Software Asset Management
 Develop an IT Asset Management Strategy
Develop an IT Asset Management Strategy
 Reduce Shadow IT With a Service Request Catalog
Reduce Shadow IT With a Service Request Catalog
 Harness Configuration Management Superpowers
Harness Configuration Management Superpowers
 Prepare and Defend Against a Software Audit
Prepare and Defend Against a Software Audit
 M&A Runbook for Infrastructure and Operations
M&A Runbook for Infrastructure and Operations
 IT Asset Management (ITAM) Market Overview
IT Asset Management (ITAM) Market Overview




