- The security team is unsure of governance needs and how to manage them.
- There is a lack of alignment between key stakeholder groups
- There are misunderstandings related to the role of policy and process.
Our Advice
Critical Insight
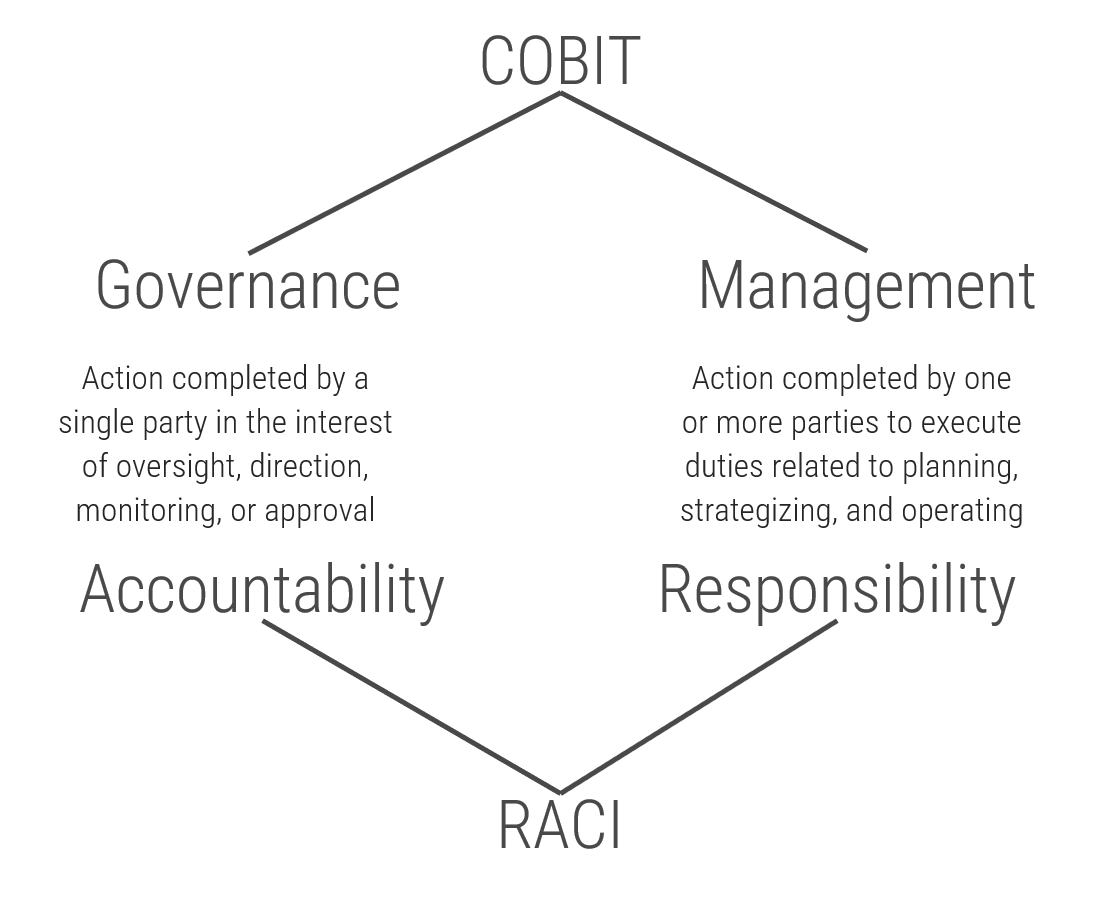
Good governance stems from a deep understanding of how stakeholder groups interact with each other and their respective accountabilities and responsibilities. Without these things, organizational functions tend to interfere with each other, blurring the lines between governance and management and promoting ad–hoc decision making that undermines governance.
Impact and Result
- The first phase of this project will help you establish or refine your security governance and management by determining the accountabilities, responsibilities, and key interactions of your stake holder groups.
- In phase two, the project will guide you through the implementation of essential governance processes: setting up a steering committee, determining risk appetite, and developing a policy exception-handling process.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
10.0/10
Overall Impact
$19,350
Average $ Saved
13
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Donor Network West
Guided Implementation
10/10
$13,700
5
getting expert understanding in this space is very important to our organization. worst part is when the models don't have clear definition on the ... Read More
ATS CORPORATION
Guided Implementation
10/10
$25,000
20
Fritz Jean-Lois provided valuable guidance in quickly developing our security governance and management plan to support our goal of maturing the se... Read More
Sage Therapeutics
Workshop
10/10
N/A
N/A
The workshop was very insightful and I enjoyed the workshop immensely. Working through the charters and learning how to maximize our use of the to... Read More
NMB BANK PLC.
Guided Implementation
10/10
$12,599
50
The best experience was when Logan was explaining to me different options available with infotech, that opened my eyes for change of direction on m... Read More
The University Of Manchester
Guided Implementation
9/10
$152K
20
Wonder Brands Inc.
Guided Implementation
8/10
N/A
5
DAI Global, LLC
Guided Implementation
9/10
$12,399
5
I very much appreciate the knowledgeable experts who helped us quickly understand an approach to get our arms around a way to move forward with eva... Read More
Elementis Specialties
Guided Implementation
10/10
N/A
120
City of Kirkland
Guided Implementation
10/10
N/A
N/A
Allegis
Guided Implementation
10/10
$2,546
5
Filipe is very knowledgeable on the topic and the other resources that Infotech has available.
Clark Schaefer Hackett
Guided Implementation
10/10
$3,820
20
Having Kevin's expertise to help me through this project was very helpful.

Security Management
Establish the missing bridge between security and the business to support tomorrow's enterprise with minimal resources.
- Course Modules: 3
- Estimated Completion Time: 1 hour




 Assess and Manage Security Risks
Assess and Manage Security Risks
 Assess Your Cybersecurity Insurance Policy
Assess Your Cybersecurity Insurance Policy
 Achieve Digital Resilience by Managing Digital Risk
Achieve Digital Resilience by Managing Digital Risk
 Prevent Data Loss Across Cloud and Hybrid Environments
Prevent Data Loss Across Cloud and Hybrid Environments
 Build an IT Risk Management Program
Build an IT Risk Management Program
 Develop and Deploy Security Policies
Develop and Deploy Security Policies
 Fast Track Your GDPR Compliance Efforts
Fast Track Your GDPR Compliance Efforts
 Build a Security Compliance Program
Build a Security Compliance Program
 Embed Privacy and Security Culture Within Your Organization
Embed Privacy and Security Culture Within Your Organization
 Establish Effective Security Governance & Management
Establish Effective Security Governance & Management
 Improve Security Governance With a Security Steering Committee
Improve Security Governance With a Security Steering Committee
 Develop Necessary Documentation for GDPR Compliance
Develop Necessary Documentation for GDPR Compliance
 Reduce and Manage Your Organization’s Insider Threat Risk
Reduce and Manage Your Organization’s Insider Threat Risk
 Satisfy Customer Requirements for Information Security
Satisfy Customer Requirements for Information Security
 Master M&A Cybersecurity Due Diligence
Master M&A Cybersecurity Due Diligence
 Integrate IT Risk Into Enterprise Risk
Integrate IT Risk Into Enterprise Risk
 Present Security to Executive Stakeholders
Present Security to Executive Stakeholders
 Deliver Customer Value by Building Digital Trust
Deliver Customer Value by Building Digital Trust
 Address Security and Privacy Risks for Generative AI
Address Security and Privacy Risks for Generative AI
 Protect Your Organization's Online Reputation
Protect Your Organization's Online Reputation
 Develop an AI Compliance Strategy
Develop an AI Compliance Strategy
 Get Started With AI Red-Teaming
Get Started With AI Red-Teaming
 Achieve CMMC Compliance Effectively
Achieve CMMC Compliance Effectively
 Building Info-Tech’s Chatbot
Building Info-Tech’s Chatbot
 Building the Road to Governing Digital Intelligence
Building the Road to Governing Digital Intelligence
 An Operational Framework for Rolling Out AI
An Operational Framework for Rolling Out AI
 Discover and Classify Your Data
Discover and Classify Your Data




