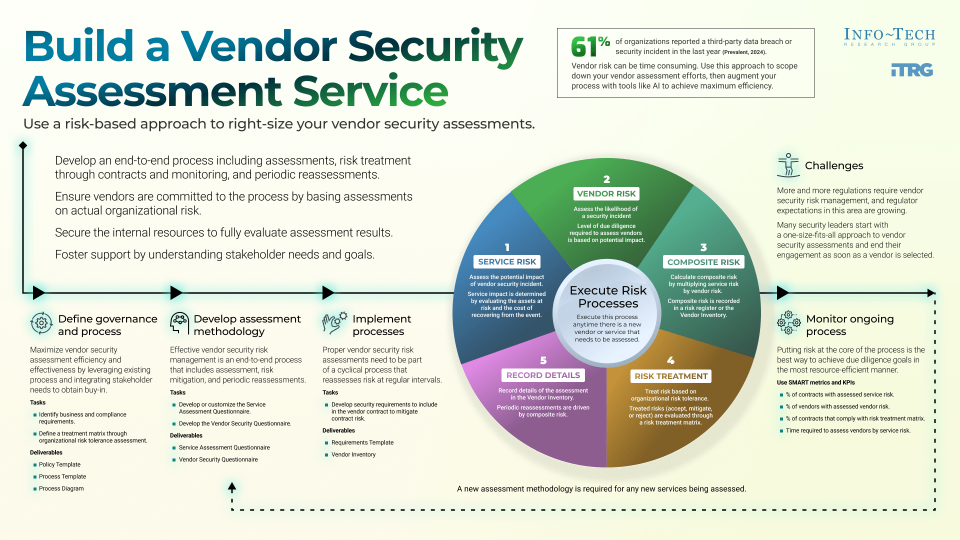
As organizations increasingly rely on third-party vendors to support critical objectives, they also open themselves up to more security risks and points of entry for malicious actors. An effective and efficient security assessment process is essential to managing this risk. Our framework helps security leaders streamline their vendor assessment process and create right-sized vendor security plans for your organization’s needs.
Vendor security risk management is a growing concern for many organizations, and regulatory expectations in this area are also growing. However, traditional approaches to vendor security assessments are seen by business partners and vendors as too onerous and are unsustainable for information security departments. A right-sized vendor security assessment service will efficiently manage risk, meet requirements, and leave more time to address critical threats.
1. Right-size the process with a risk-based approach
Putting risk at the core of your assessment process is the best way to meet your vendor due diligence goals. Security assessments are time-consuming for both you and your vendors – maximize the returns by scaling your assessments to the associated risk and access provided. Not all vendors are the same, so taking a one-size-fits-all approach is a fast way to lose time, resources, and vendors.
2. Include all key players from the get-go
An effective and efficient assessment process can only be achieved when all key players are participating. Identifying business requirements, customer expectations, and compliance obligations will require input from many areas of your organization. Take the time to include all key players from the beginning and leverage existing processes to aid your requirement discovery.
3. Design an end-to-end process
A one-and-done process for vendor security can introduce risks that grow in the shadows without proper visibility. Though your initial contract with a vendor may involve minimal risk, new work and additional risk may be added as your relationship with the vendor develops. Effective vendor security risk management is an end-to-end process that must involve periodic reassessments.
Use our comprehensive framework to establish a risk-based vendor security assessment program
Use this step-by-step framework, featuring a robust set of tools and templates, to establish, evaluate, and maintain your right-sized vendor security assessment program. Our framework incorporates your existing security policies and provides customizable questionnaire templates aligned with risk tolerance and service level to assess vendors.
- Scale your assessment to the level of risk given to each vendor and the scope of their service.
- Leverage AI to augment your assessment process and accelerate audit report reviews.
- Monitor the process to avoid outdated security assessments and changing regulatory requirements.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
8.3/10
Overall Impact
$6,805
Average $ Saved
8
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
City of Santa Fe
Guided Implementation
10/10
N/A
N/A
I am most grateful for Jon Nelson's help as an InfoTech Analyst with guiding me and my team towards a working Cyber Security Strategic Plan and man... Read More
The Pittsburgh Water and Sewer Authority
Guided Implementation
10/10
N/A
20
Jon is very knowledgeable about Info-Tech tools and is able to provide helpful answers to all of our questions. For example, on the recent call he... Read More
US Senate
Guided Implementation
3/10
N/A
5
Petar was very knowledgeable SME. He shared valuable information, materials and gave solid advice for our initiative. Petar also provided us the op... Read More
The University of North Carolina System Office
Guided Implementation
7/10
$2,603
4
Access to ready templates. Worst part is the manual manner in which I will have to use the templates.
Nippon Sanso Holdings Corporation
Guided Implementation
8/10
$5,919
4
Cidel Bank & Trust
Guided Implementation
10/10
$13,700
5
no worse parts. Everything was well presented with Jon providing valuable insight on the importance of monitoring and managing vendor risk and h... Read More
Westoba Credit Union Limited
Guided Implementation
10/10
$5,000
10
It's really valuable to have this work ready to be used instead of building it myself.










 Develop and Implement a Security Incident Management Program
Develop and Implement a Security Incident Management Program
 Build Resilience Against Ransomware Attacks
Build Resilience Against Ransomware Attacks
 Build a Vendor Security Assessment Service
Build a Vendor Security Assessment Service
 Implement Risk-Based Vulnerability Management
Implement Risk-Based Vulnerability Management
 Improve Organizational Resilience With a Tabletop Program
Improve Organizational Resilience With a Tabletop Program
 Master Your Security Incident Response Communications Program
Master Your Security Incident Response Communications Program
 Design a Coordinated Vulnerability Disclosure Program
Design a Coordinated Vulnerability Disclosure Program







