- Mounting pressure from increasingly complex operations, a growing threat landscape, and stricter regulations are forcing leaders to bridge the gap between planning and execution.
- Failure to demonstrate operational resilience when responding to incidents, recovering systems, and continuing operations can result in significant financial and reputational damage.
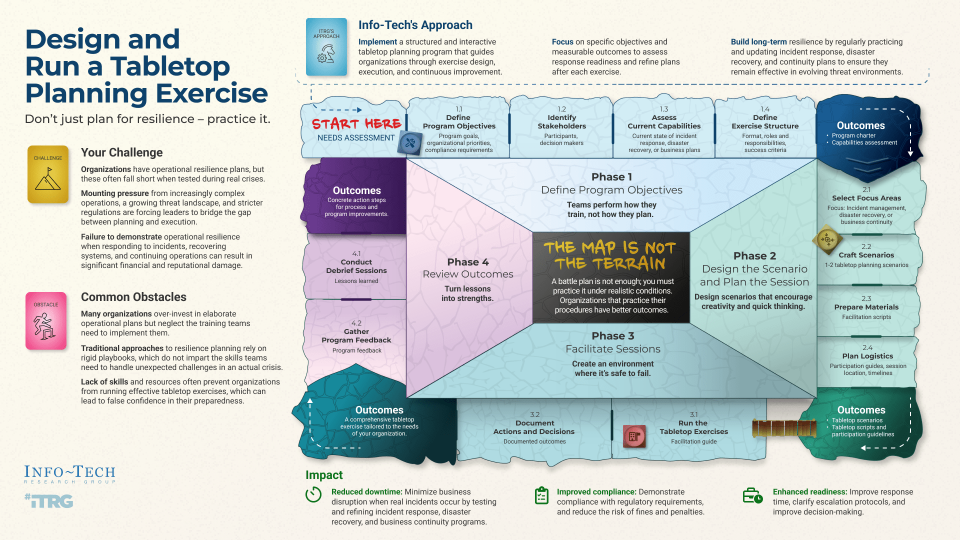
- Traditional approaches to resilience planning rely on rigid playbooks, which do not impart the skills teams need to handle unexpected challenges in an actual crisis.
Our Advice
Critical Insight
- The map is not the terrain.
- A plan is not enough; you must practice it under realistic conditions. Organizations that practice their procedures have better outcomes.
Impact and Result
- Implement a structured and interactive tabletop planning program that guides organizations through exercise design, execution, and continuous improvement.
- Focus on specific objectives and measurable outcomes to assess response readiness and refine plans after each exercise.
- Build long-term resilience by regularly practicing and updating incident response, disaster recovery, and continuity plans to ensure they remain effective in evolving threat environments.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
10.0/10
Overall Impact
$16,861
Average $ Saved
14
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Champaign Residential Services Inc
Guided Implementation
10/10
N/A
N/A
Thank you for going over the blueprint and giving me an idea of each step of the process. Looking forward to working on this in the fall :-)
New Brunswick Community College (NBCC)
Guided Implementation
10/10
$2,000
2
The guided discussions and material reviews, along with the online resources, were crucial in designing, executing, and reviewing our institution's... Read More
Long Island Power Authority
Guided Implementation
10/10
$28,085
20
Able to schedule time with experts and the. Utilize the expert as a coach to bounce back ideas.
Corporation Of The City Of Orillia
Guided Implementation
10/10
$20,500
20
Erik was great to work with and has so much knowledge. We had a quote from a third party for a table top exercise at $15,000 cdn. This saved us eno... Read More
American Bankers Association
Guided Implementation
10/10
$12,599
5
Michele was great - very flexible with his scheduling, very hands one, knowledgeable. worst part - we aren't quite done with table tops to validat... Read More
Workshop: Improve Organizational Resilience With a Tabletop Program
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
Module 1: Define program objectives
The Purpose
Define program objectives.
Key Benefits Achieved
Understand program objectives.
Activities
Outputs
Define purpose and scope.
Identify program resources.
Review program criteria and milestones.
- Program charter
Review capability assessment.
- Capability assessment
Module 2: Design scenario and plan sessions
The Purpose
Design scenario and plan sessions.
Key Benefits Achieved
Complete scenario and plan for tabletop session.
Activities
Outputs
Define exercise concept.
- Exercise format and logistics
Design scenarios.
- 1-2 tabletop scenarios customized to your environment
Prepare materials.
- Completed tabletop facilitation scripts with discussion prompts and assessment metrics
Plan logistics.
Module 3: Facilitate sessions
The Purpose
Facilitate sessions.
Key Benefits Achieved
Completed tabletop sessions.
Activities
Outputs
Run sessions.
- Facilitated tabletop planning sessions with technical and leadership groups.
Document actions and decisions.
Module 4: Review outcomes
The Purpose
Review outcomes.
Key Benefits Achieved
Understand lessons and recommendations from sessions.
Activities
Outputs
Debrief sessions.
- Documented lessons learned from the sessions.
Gather program feedback.
- Feedback on the tabletop planning program.
Process improvement opportunities.










 Develop and Implement a Security Incident Management Program
Develop and Implement a Security Incident Management Program
 Build Resilience Against Ransomware Attacks
Build Resilience Against Ransomware Attacks
 Build a Vendor Security Assessment Service
Build a Vendor Security Assessment Service
 Implement Risk-Based Vulnerability Management
Implement Risk-Based Vulnerability Management
 Improve Organizational Resilience With a Tabletop Program
Improve Organizational Resilience With a Tabletop Program
 Master Your Security Incident Response Communications Program
Master Your Security Incident Response Communications Program
 Design a Coordinated Vulnerability Disclosure Program
Design a Coordinated Vulnerability Disclosure Program






