- The rise of attacks through identity compromise demonstrates the focus attackers are placing on leveraging identities to infiltrate a network.
- Traditional authentication methods are no longer safe, as each authentication request puts the enterprise at risk.
- There is a lack of visibility into the different authentication practices an organization implements.
Our Advice
Critical Insight
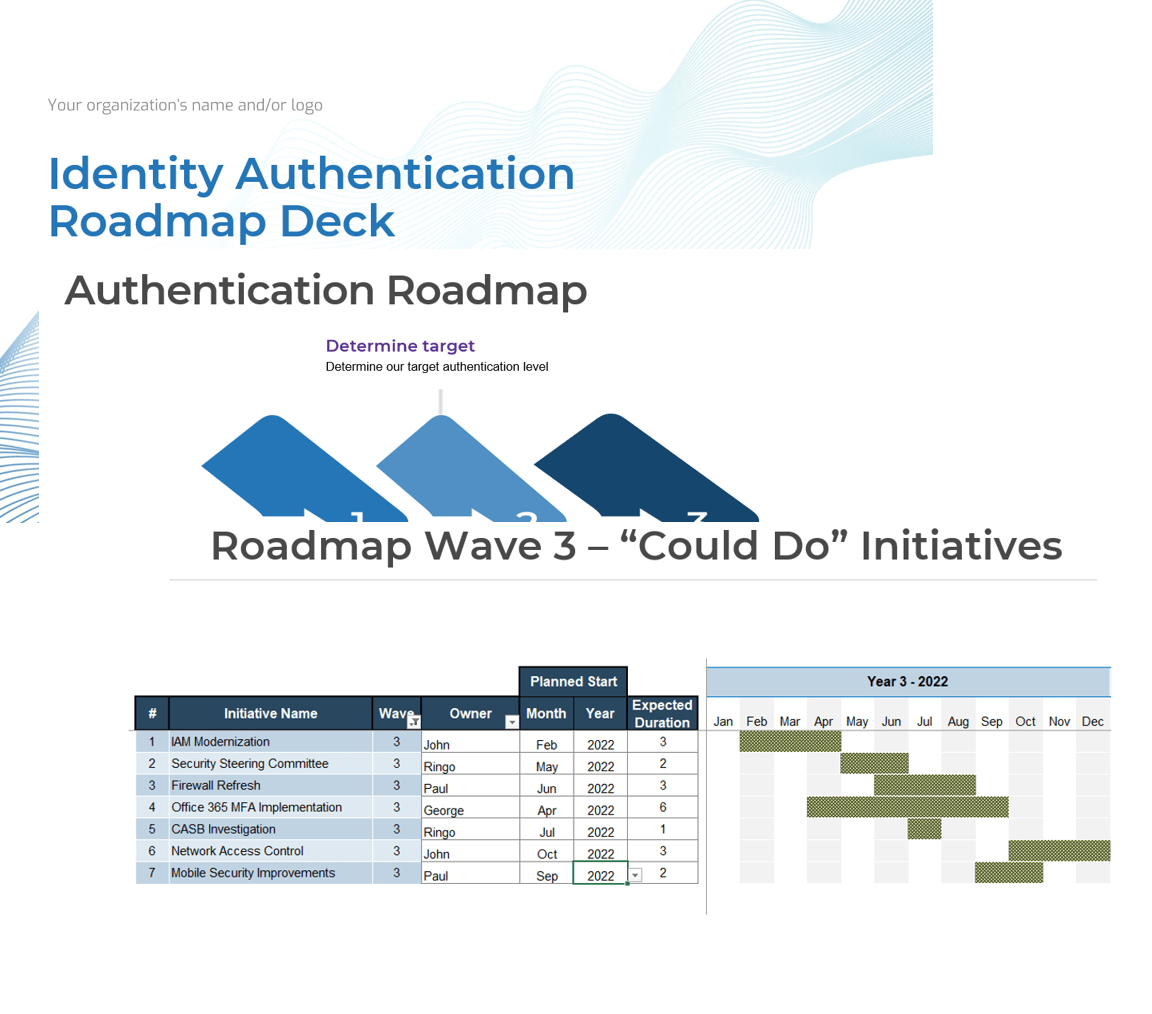
- Leveraging a risk-based approach to modernizing your authentication practices will ensure you have the right authentication assurance level in place while also identifying continuous improvement for your authentication lifecycle.
- Every authentication assurance level possesses its own benefits ands risks, hence you should target the authentication methods that aligns with your risk profile.
- Begin your modernized authentication roadmap by prioritizing your authentication practices for the identities that are the most critical to your organization.
- Implementing the right solution for your authentication needs begins by formalizing the right policies to ensure it aligns with your goals.
- A robust authentication practice will mature your IAM and provide you with the visibility to safeguard your most critical protect surfaces
- Not all organizations possess the appropriate readiness to modernize their identity authentication practices; it’s important to assess your current maturity before identifying improvement actions.
Impact and Result
This blueprint will provide you with:
- A guideline on how to assess your current authentication practices and determine which authentication assurance levels and practices meet your needs.
- Visibility into your organization’s current authentication practices within your various identity repositories.
- A developed roadmap to help you determine how to prioritize your authentication initiatives based on risk, organizational needs, and capabilities.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
9.5/10
Overall Impact
$18,495
Average $ Saved
8
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
ESS Tech, Inc
Guided Implementation
10/10
$34,250
10
Best - A solution out there (InfoTech shared options) that avoids purchase of another ecosystem for CyberSecurity. Technical conversation confirmed... Read More
Kyocera SGS Precision Tools
Guided Implementation
10/10
N/A
N/A
Actual industry knowledge.
Randolph Brooks Federal Credit Union
Guided Implementation
10/10
$2,740
5
Great feedback from the advisor.
Shared Services Canada - Chief Information Office
Guided Implementation
8/10
N/A
N/A
Greatly appreciated the strategic discussion without focus on the day to day. Appreciate the materials sent after the meeting also. thank you.






 Assess and Govern Identity Security
Assess and Govern Identity Security
 Develop a Comprehensive IAM Improvement Strategy
Develop a Comprehensive IAM Improvement Strategy
 Simplify Identity and Access Management
Simplify Identity and Access Management
 Passwordless Authentication
Passwordless Authentication
 Modernize Your Identity Authentication Practices
Modernize Your Identity Authentication Practices




